Written by Rainer Gerhards (2008-07-03)
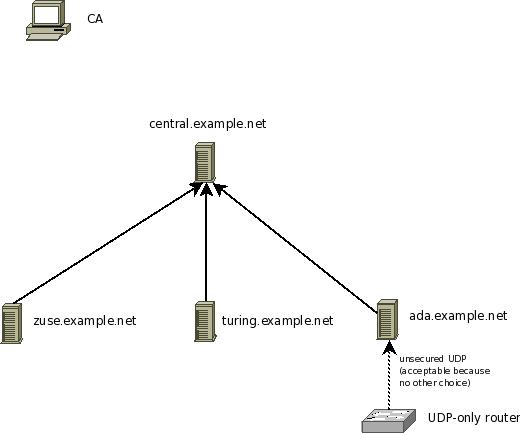
In this step, we configure the UDP relay ada.example.net. As a reminder, that machine relays messages from a local router, which only supports UDP syslog, to the central syslog server. The router does not talk directly to it, because we would like to have TLS protection for its sensitve logs. If the router and the syslog relay are on a sufficiently secure private network, this setup can be considered reasonable secure. In any case, it is the best alternative among the possible configuration scenarios.

Steps to do:
These were essentially the same steps as for any TLS syslog client. We now need to add the capability to forward the router logs:
At this point, please be reminded once again that your security needs may be quite different from what we assume in this tutorial. Evaluate your options based on your security needs.
Keep in mind that this rsyslog.conf sends messages via TCP, only. Also, we do not
show any rules to write local files. Feel free to add them.
# start a UDP listener for the remote router
$ModLoad imudp # load UDP server plugin
$AllowedSender UDP, 192.0.2.1 # permit only the router
$UDPServerRun 514 # listen on default syslog UDP port 514
# make gtls driver the default
$DefaultNetstreamDriver gtls
# certificate files
$DefaultNetstreamDriverCAFile /rsyslog/protected/ca.pem
$DefaultNetstreamDriverCertFile /rsyslog/protected/machine-cert.pem
$DefaultNetstreamDriverKeyFile /rsyslog/protected/machine-key.pem
$ActionSendStreamDriverAuthMode x509/name
$ActionSendStreamDriverPermittedPeer central.example.net
$ActionSendStreamDriverMode 1 # run driver in TLS-only mode
*.* @@central.example.net:10514 # forward everything to remote server
Be sure to safeguard at least the private key (machine-key.pem)! If some third party obtains it, you security is broken!
Copyright © 2008 Rainer Gerhards and Adiscon.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license can be viewed at http://www.gnu.org/copyleft/fdl.html.